Title II, exhibition view, Galerie Antoine Ertaskiran, Montréal (Canada)
04 apr.— 5 may. 2018
5
may.
2018
AUDE PARISET
CATHERINE TELFORD-KEOGH
DENA YAGO
DIS
GOLDIN+SENNEBY
JASON MATTHEW LEE
NINA CANELL
SIMON DENNY
CURATED BY VIE D’ANGE & CHRISTOPHER KULENDRAN THOMAS
Galerie Antoine Ertaskiran is pleased to present the second installment of a two-part collaboration with Montreal-based project space Vie d’ange. Departing from the previous exhibition, Our Thing – which considered the ways in which crowds are organized by technological influences – Title II explores the concept of ’net neutrality’ and the promise of an open and egalitarian communications network. Together the works in this exhibition examine notions of fragmentation, both of language and of form, whilst considering historical forces which reveal the fraught asymmetries of power embedded within communications infrastructures. These works are presented as materializations of truncated narratives to question a mediascape where some content loads faster than others.
1. The 1996 Telecommunications Act was the first major overhaul of telecommunications law in the United States since the Federal Communications Commission was founded at the dawn of the Second World War in 1934. During the signing ceremony, Bill Clinton used the same pen Dwight D. Eisenhower had used to sign the Federal Highway Act of 1956, before proceeding to sign a digital copy of the bill across a touchscreen surface1 – making the 1996 Telecommunications Act the first piece of legislation signed in cyberspace.2
2. The 1990’s saw a new era defined by a techno-optimist spirit as well as the market confidence of the dot-com bubble. Meanwhile, the opening up of previously inaccessible geopolitical markets enabled the global dominance of the neoliberal order. Speaking at the signing ceremony of the 1996 Telecommunication Act, Democratic from Senator Fritz Hollings (D) of South Carolina declared: “As of now the Berlin Wall of telecommunications has been demolished”.3
3. Under Title II of the act, a diversity of communications streams such as broadcast television, landline and mobile telephony – and for the first time ever the Internet – were bundled under one piece of legislation. The 1996 act cited more competition and the empowerment of American entrepreneurs and families with the freedom of more choices at lower costs. It effectively deregulated the Internet and opened up public utilities to private enterprise. However, until late 2017 under Title II, Internet Service Providers (ISPs) were prohibited from creating artificial scarcity by throttling content. Throttling would allow ISPs to capitalize upon the creation of fast and slow content traffic lanes. Opponents of such free-market deregulation feared the precedent where not all content would load equally as a logical first step to some content not being able to load at all. In anticipation of this year’s repeal of Title II, DIS produced Polimbo, a website-survey that acts as a political compass on the issue of net neutrality, presented in the exhibition on a phone that’s charging behind the gallery’s reception desk. Occasionally accessible in the gallery’s adjacent space, Goldin+Senneby’s After Microsoft… tells the story of how a California hillside came to collide with a global branding strategy.
4. Speed of access becomes the predominant aesthetic in the wake of a deregulated communication-scape. The work in this exhibition comes together as fragmentations of both language and form, presenting a series of truncated narratives which materialize in a half-loaded format of dis-connectivity. Nina Canell’s subterranean fibre optic cable sheathings are gathered from high-grade cables employed in Korean communication networks. Not yet introduced in European and North American infrastructures, these cables are already being replaced in Korea.
5. Jason Matthew Lee’s work with modified payphones and payphone shells express the early hacking cultures of network exploration known as ‘phreaking’4. Lee’s works bare a connection to Canell’s emptied out cable skins which also engage with the real passageways of communication infrastructures to evoke a visceral vocality.
6. Just as Lee and Canell’s works are cut off and segmented from a larger network, the exhibition presents an incomplete selection of canvases from Simon Denny’s scalable body of work The Personal Effects of Kim Dotcom. Since 2013 Denny has chronicled an ongoing portrait of Internet entrepreneur turned activist Kim Schmitz through an iterative documentary style exhibition-making practice.5 Kim Dotcom’s website Megaupload was one of the most visited file-sharing platforms until his assets, servers and websites were seized in a high profile FBI raid on his New Zealand compound.6
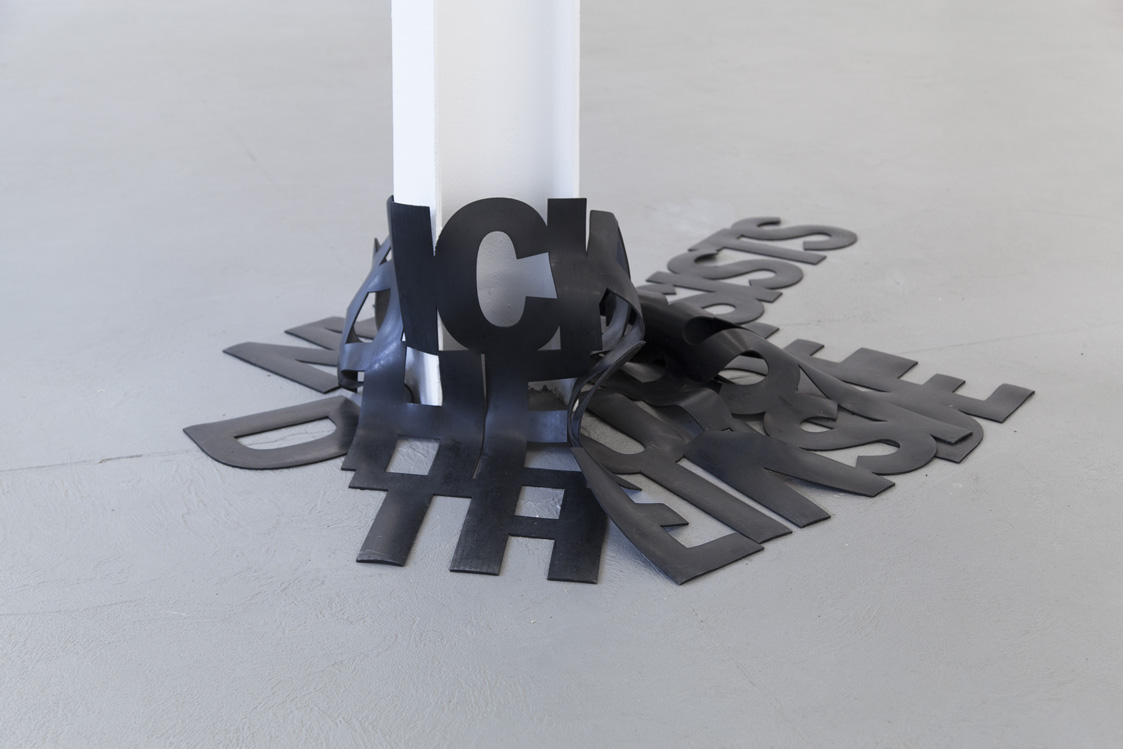
7. The work of Dena Yago and Catherine Telford-Keogh equally deal with the entanglement and congestion of language when physicalized into tangible forms. Dena Yago’s CNC’d rubber text works speak to the perennial ways in which form obfuscates and redefines the reception of language. Her work Remove the Outside and the Inside Remains recalls the gestures of deregulation to ‘remove’ and ‘cut away to the essential’. Considering Yago’s work in relation to Nina Canell’s dislocated cable sheathings, the transmutability of materials make apparent how material can be the conduit for information while equally being the information itself. Catherine Telford-Keogh’s work slows the outside world by materializing into hardened pools and large panes of confinement. Telford-Keogh draws on an interest in phonetics and form to explore a sensory memory that internalizes the ways that language shapes material.7
8. Aude Pariset’s Promession® #1 remains from the previous exhibition at the gallery. This work comprises a colony of mealworms which have been eating away at styrofoam while hermetically encased in a bed frame. This ecosystem has both matured and deteriorated into an uneven state; where some worms have perished, others keep eating and some have transformed into beetles leaving skin sheddings in their wake.
1. Lamolinara, Guy (19 February 1996). “Wired for the Future: President Clinton Signs Telecom Act at LC”. Library of Congress. Retrieved 22nd March 2018.
2. In response to Clinton and Gore’s symbolic foray of establishing law in cyber space, the cyber-libertarian John Perry Barlow – an American poet, essayist and lyric writer for the Grateful Dead – wrote his influential manifesto A Declaration for Cyber Independence, proclaiming: “Governments of the Industrial World, you weary giants of flesh and steel, I come from Cyberspace, the new home of Mind. On behalf of the future, I ask you of the past to leave us alone. You are not welcome among us. You have no sovereignty where we gather”.
Perry Barlow, John. (8 February 1996, Davos Switzerland.) “A Declaration of the Independence of Cyberspace”. Electronic Frontier Foundation. Retrieved 20th March 2018.
3. Signing of the 1996 Telecommunications Act. Al Gore (Introduction), Bill Clinton (Address), Sen Frtiz Hollings (D) Closing Address).” C-SPAN, Washington, D.C. 8 February. 1996.
4. As a predecessor to computer hacking, the subculture of Phreaking emerged alongside cybernetics and within the political turmoil of the late 1960’s. Apple co-founder Steve Wozniak cites Phreaking as a profound influence upon him as a young programmer. In her essay Phreaks, Hackers and Trolls: The Politics of Transgression and Spectacle, Gabriella Coleman describes how communications law evolved in response to Phreaking by citing Ursula Le Guin: “To Make a Thief, Make an Owner; to Create Crime, Create Laws”.
5. Denny has indexed the 110 items seized by the US Government and rematerialized them as inkjet printed canvases, often exhibiting the canvases with copies and replicas of the seized property. According to the artist, these seized possessions represent a sort of venn diagram of shared systems of value between Kim Dotcom and the US Authorities. The Grand Jury indictment is printed and displayed next to the canvases. It includes a full list of the seized property.
6. During the 1990’s, as a teenager, Kim Schmitz (better known as Kim Dotcom) used to hack the databases of AT&T and other major phone companies. Exploiting the vulnerabilities of an emerging global telecoms infrastructure, it is alleged that Schmitz made bulk purchases of stolen phone card information from American hackers. Schmitz then set up premium chat lines in Hong Kong and in the Caribbean and used a “war dialer” program to call the lines en masse with the stolen card numbers – generating over €50,000 in ill-gained profits.
Gallagher, Sean (26 January 2012). “The Fast, Fabulous, Allegedly Fraudulent Life of Megaupload’s Kim Dotcom”. Wired. Retrieved 24th March 2018.
7. Through an expansive inventory of mass produced consumables, such as trademarked food items and institutional cleaning products, Catherine Telford-Keogh’s work amasses a material economy of the everyday to conjure an uncanny encounter – where recollection of material memory overcomes a sanitization of the senses.